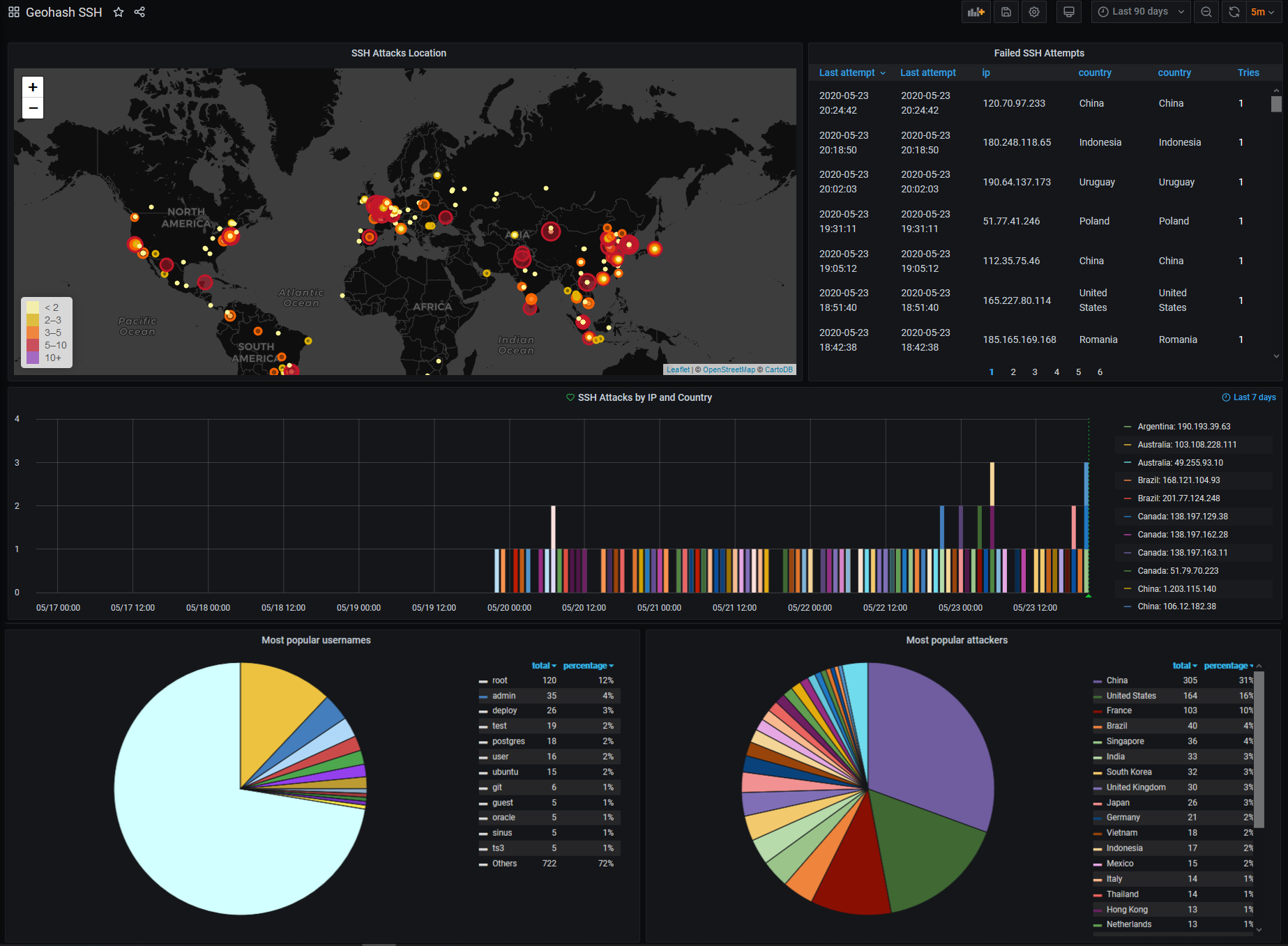
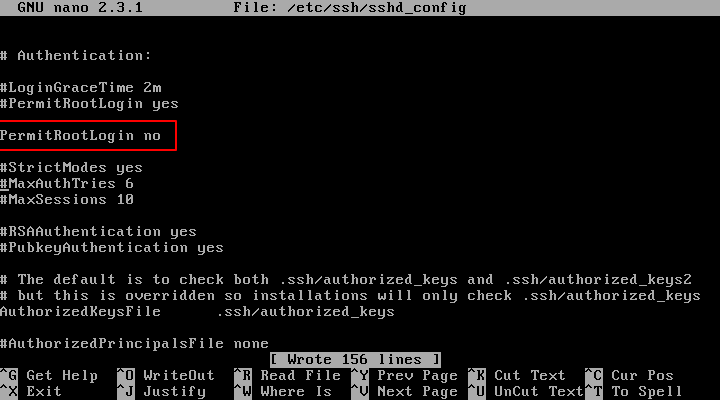
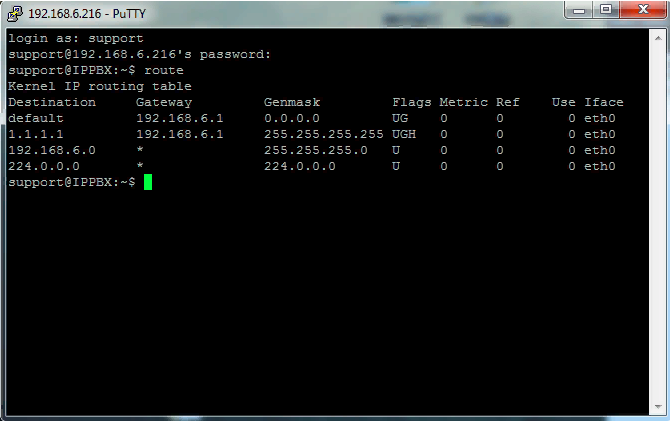
Ubuntu - Failed logging attempts on blocked ports (SSH doesn't listen on those ports) - Server Fault

Yet another ssh brute force attack and how to protect against it with iptables and sshguard – The GNU of Life, the Universe and Everything
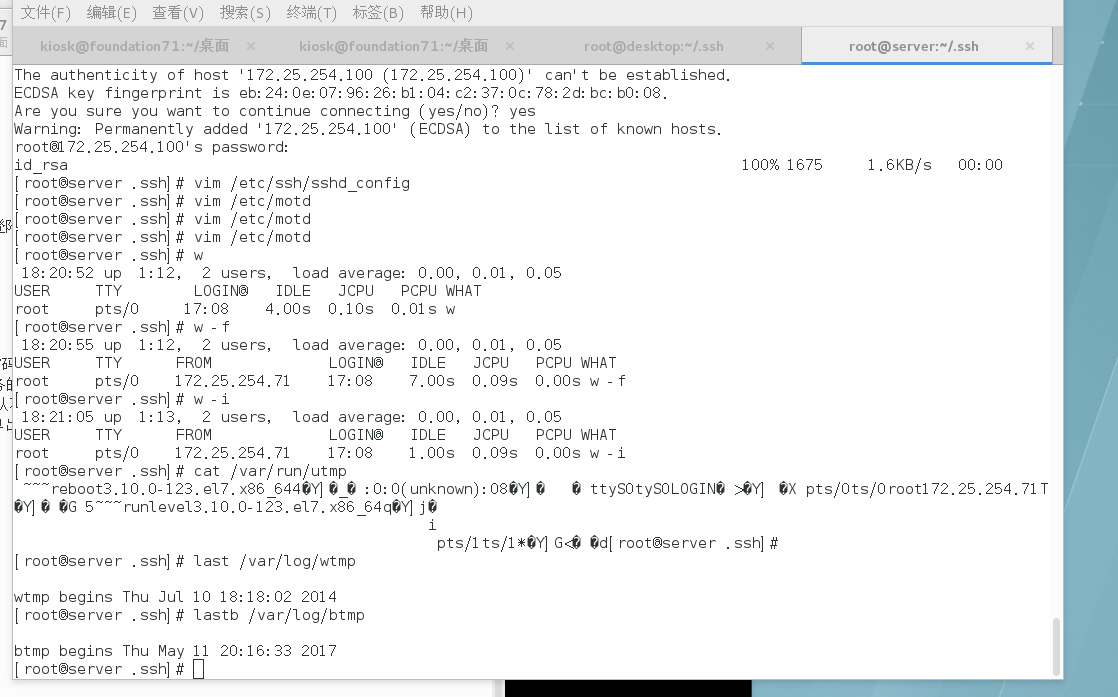
unit7, linux ssh secure connection, change ssh configuration file, see ssh login situation | LaptrinhX
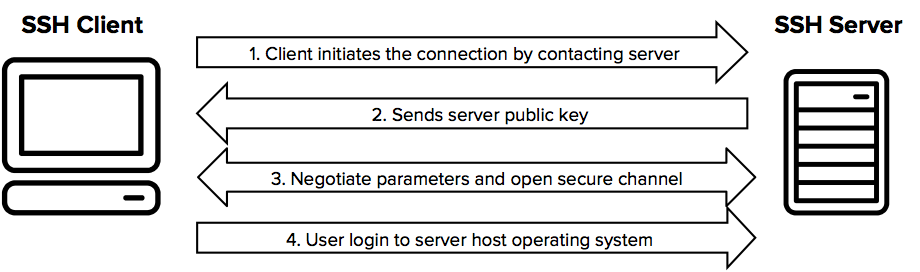
SSH protocol is the standard for strong authentication, secure connection, and encrypted file transfers. We developed it.

Is it possible to have 2 ports open on SSH with 2 different authentication schemes? - Unix & Linux Stack Exchange